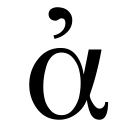📚 Agora location [[2003 12 23 is the pstn more secure]] ☆
Agora locations contain community contributions with titles or topics that match your search.
📄 _posts/archive/2003-12-23-is-the-pstn-more-secure.md by @bmann ☆ raw
layout: post title: Is the PSTN more secure? created: 1072239064 categories:
- VoIP
I was just thinking, that perhaps one of the most advantageous features of the PSTN is it’s security :-). It is not possible to do a DOS attack (or other malicious activities) on a POTS line, unlike a IPPhone. (Or are all these issues resolved.)
For example is it possible for me to disrupt an existing conversation, but flooding an existing IP phone with requests? Ow! :-(. Or is this and others trivial scenarios?
Comments?
✨ AI Synthesis Mistral Gemini ChatGPT Claude
Expanding this section will automatically generate an AI synthesis of the contributions in this node.